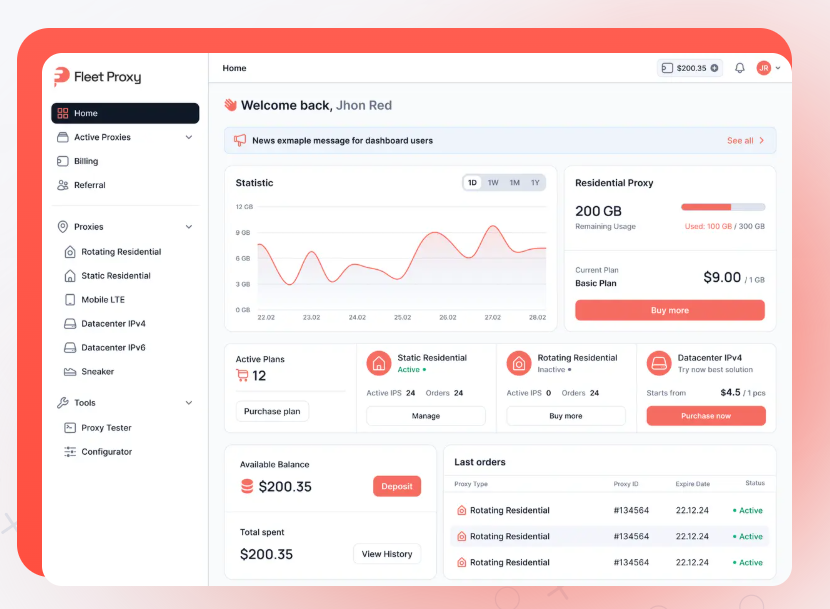
Changing fonts and masking WebGL used to be enough. You’d tweak the resolution, run a fresh profile, and the browser would slip past most detection gates. That held when surface signals were the only thing being checked.
Those days are done.
Detection systems now read deeper, pulling session behavior from the network itself, long before the fingerprint gets rendered.
Tools like GemLogin play a crucial role. They give users full control over what the browser looks like. You can build separate profiles, apply noise to your canvas fingerprint, and simulate realistic environments across different devices. That’s what makes antidetect browsers valuable in any session-based workflow.
But even a perfect profile falls apart when the network traffic underneath tells a different story. The fingerprint might say you’re running a machine in Tokyo with a fresh install, but the request arrives through an IP that’s been flagged five times in the last hour, or a resolver that doesn’t line up with the timezone setting.
Detection logic runs deeper than the browser now. It checks how requests behave long before the page starts loading.
Detection Has Moved Below the Surface
The fingerprint still matters. It shapes how the front-end behaves and determines whether your browser renders correctly. But it no longer decides the outcome by itself. Detection stacks track more than the browser.
Here’s what systems look for now:
- Resolver patterns that don’t match declared location
- Session reuse across unrelated tasks
- Identical request pacing across different accounts
- TTL anomalies that don’t reflect real-world navigation
- ASN ranges that rotate too frequently
- Geolocation vs browser mismatch
- Historical overlap with flagged traffic
A tool like GemLogin controls what the browser says about the user. That’s essential. But everything after that depends on how the traffic looks, how it lands, and how often the same IP structure repeats itself across sensitive flows. Most failures don’t come from the fingerprint. They come from the proxy.
Where Fleetproxy Fills the Gap
GemLogin helps you blend into the session. Fleetproxy helps you stay there. Once the solve begins or the flow moves from login to action, detection switches focus from browser traits to behavioral consistency. That’s where proxy behavior decides whether the session survives.
Fleetproxy was built for this layer. It doesn’t just hand you random IPs. It gives you access to a system that manages how each request moves through time, location, and session memory. That kind of stability is what keeps antidetect browsers working in high-pressure environments.
What Fleetproxy Gives You in Practice
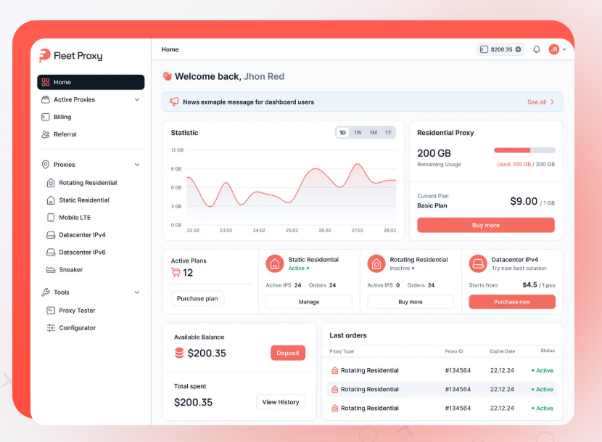
You’re not sending clean browser fingerprints into a broken traffic pipe. You’re shaping both layers together so they match the expectations of modern detection systems.
Here’s how Fleetproxy fits into GemLogin workflows:
Use Static Residential IPs
Perfect for:
- Maintaining login state over multiple steps
- Completing CAPTCHAs without triggering resets
- Running accounts that need long session memory
- Sticky IPs let you act like a real user over time, without rotation noise breaking the flow.
Deploy Mobile LTE IPs for High-Trust Tasks
Best for:
- Location-sensitive logins
- Flows where carrier networks earn better trust
- Account creation or verification
- Mobile IPs map to real-world user patterns and reduce the chance of being flagged for instability.
Run Zero-Chance Rotation for Single-Use Tasks
Useful when:
- Each request must look unique
- You can’t risk overlap
- You’re running through blacklists or flagged domains
- The IP appears once and disappears from the rotation pool immediately.
- No repeat signatures.
Segment Traffic by Tool or Campaign
Fleetproxy lets you assign different proxy pools to different actions. You can route scraper traffic separately from account logins, or isolate bot actions from live session flows. That kind of separation avoids cross-contamination and keeps flagged behavior from spreading across your setup.
Getting Started with Fleetproxy and GemLogin
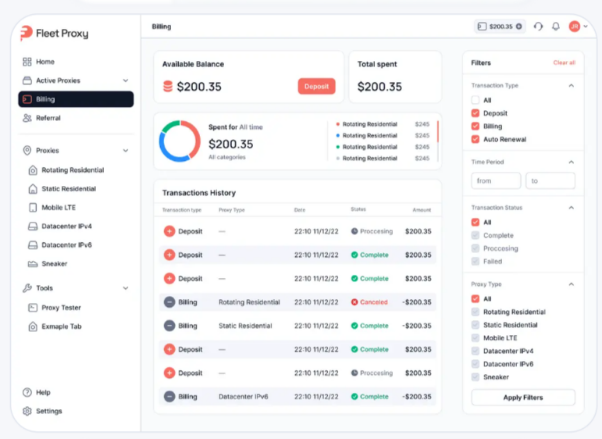
Setting up Fleetproxy with GemLogin is direct. Once you’ve created your profile inside the antidetect browser, assign the proxy credentials from your Fleetproxy dashboard. You can authenticate using IP whitelisting or username:password pairs. From there, you tag sessions by task type, assign proxy duration, and monitor usage through the live panel.
Most users start with:
- 10–25 sticky residential IPs for long session flows
- A set of zero-chance rotating LTE proxies for single-action solves
- Session tagging to separate scraping from interaction
- Usage monitoring to track TTL and reuse rate
You don’t need a separate proxy manager or plugin. Just pipe the details into GemLogin’s proxy field and start testing behavior directly against the target flows.
To help new users get started, Fleetproxy is offering 30% off your first purchase. Use the code “30OFF” during checkout and apply it to any plan.
Why Full Session Control Is No Longer Optional
Detection doesn’t fail because of missing fingerprint data alone. It fails when the traffic tells a different story. That mismatch triggers blocks more often than people realize. The setups that hold are the ones that manage both layers together.
GemLogin controls what the browser shows. Fleetproxy shapes what the network reveals underneath it. When those two stay aligned, detection systems back off. When they don’t, even solid tools start dropping sessions.
Website: gemlogin.vn